AsyncRAT Malware Hackers Use New Evasive Method
Short News:-
The AsyncRAT trojan has been distributed in an advanced phishing campaign that began in September 2021. Trojans are typically used to connect an attacker to a victim device, steal data and conduct surveillance. The sophisticated tactics allowed the malware to pass virtually undetected by most antimalware engines.
Detailed News:-
It has been reported that the AsyncRAT trojan has been distributed in an advanced phishing campaign that began in September 2021.
Morphic security researcher Michael Dereviashkin said in a report that "Through a simple email phishing tactic with an HTML attachment, threat attackers are delivering AsyncRAT (a remote access trojan) designed to remotely monitor and control its infected computers through secure, encrypted connections," he stated.
Using an email message that includes an HTML attachment disguised as an order confirmation receipt, the intrusions are launched. The message recipient is redirected to a web page that asks them to save an ISO file when they open the decoy file.
In contrast, the latest RAT campaign uses JavaScript to create an ISO file from a Base64-encoded string and mimic the download process, unlike other attacks that redirect the victim to a malicious domain.
JavaScript code embedded in the HTML receipt file generates the ISO download, not a remote server, according to Dereviashkin.
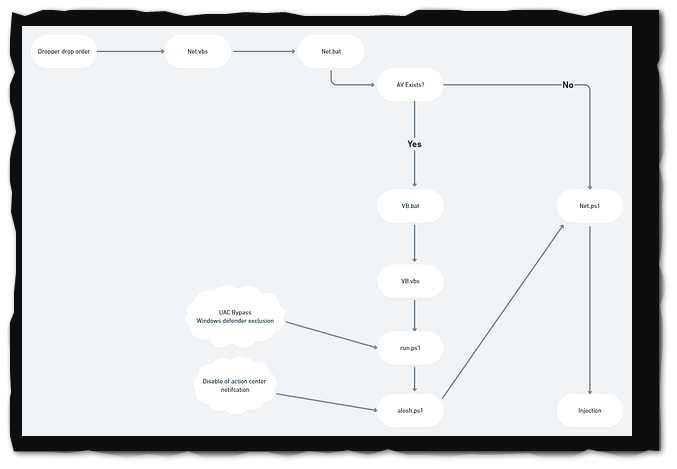
After opening the ISO file, it is automatically mounted as a DVD drive on Windows and contains either a.BAT file or a.VBS file that continues the infection chain by executing a PowerShell command.
To deliver AsyncRAT as the final payload, a.NET module is executed in-memory and acts as a dropper for three files, each of which acts as a trigger for the next. Additionally, antivirus software is checked and Windows Defender exclusions are set up.
Remote access Trojans, such as AsyncRAT, are typically used to connect an attacker to a victim device, steal data, and conduct surveillance via microphones and cameras. As a result, the intruders are able to keep tabs on and even take full control of the infected machines.
As Morphisec also noted, the campaign's advanced tactics allowed the malware to pass virtually undetected by most antimalware engines despite the operation being in effect for close to five months at the time of its release.


Post a Comment
Your suggestions and comments are welcome